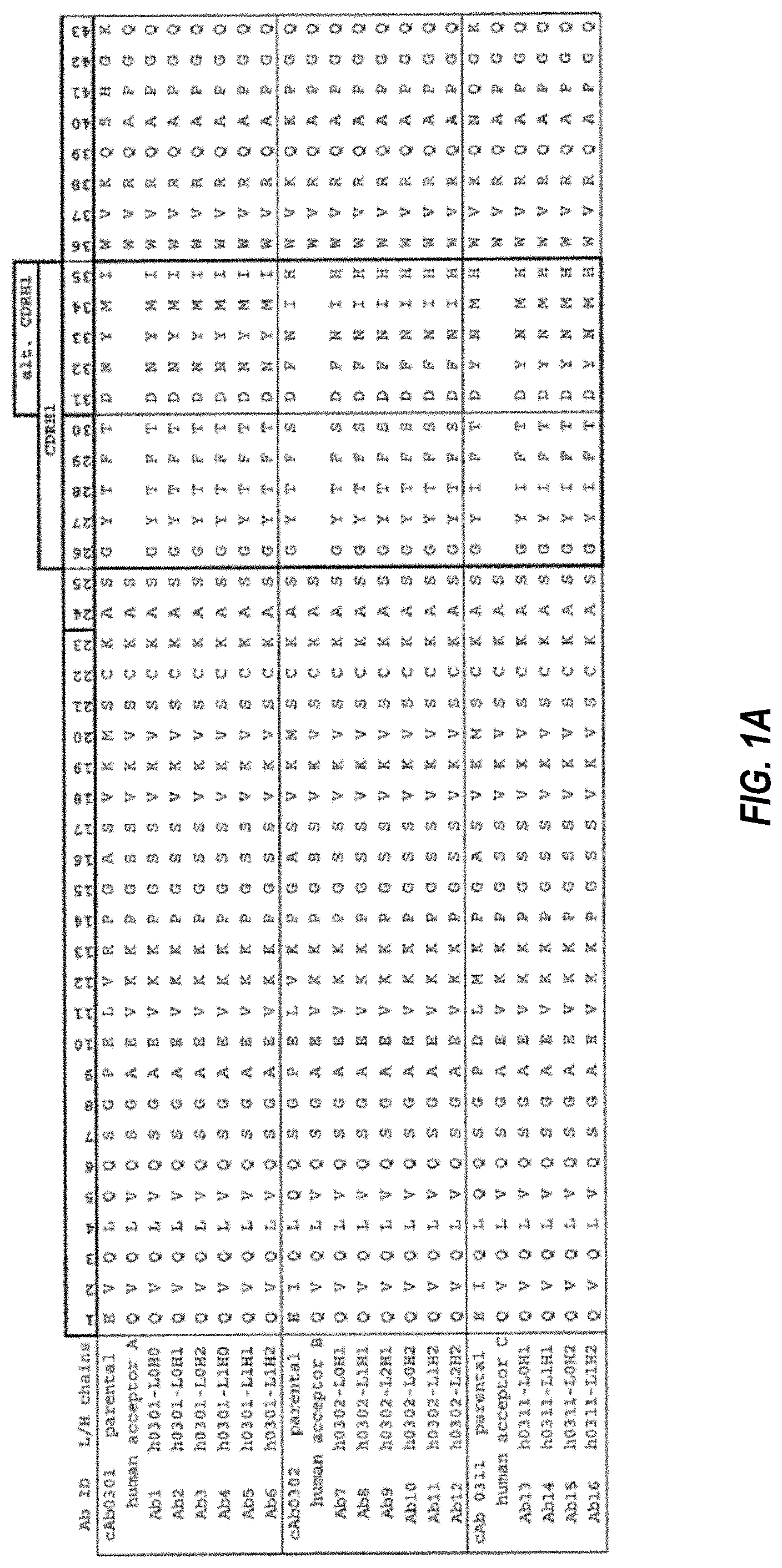
Invented by Paul DAWES, Marc Baum, Aaron Wood, IControl Networks Inc
Integrated systems refer to the combination of various components and subsystems that work together to perform a specific function or task. These systems can be found in various industries such as healthcare, automotive, manufacturing, and smart homes. Communication protocols play a crucial role in ensuring seamless connectivity and data exchange between these integrated systems.
One of the key drivers of the market for communication protocols in integrated systems is the increasing adoption of the Internet of Things (IoT) technology. IoT devices rely on communication protocols to transmit data between themselves and other devices or systems. As more and more devices become connected, the demand for communication protocols that can handle the massive amount of data being generated is growing rapidly.
Additionally, the rise of Industry 4.0 and the implementation of smart factories is fueling the demand for communication protocols in integrated systems. In smart factories, machines, sensors, and other equipment need to communicate with each other in real-time to optimize production processes and improve efficiency. Communication protocols such as OPC UA (Unified Architecture) and MQTT (Message Queuing Telemetry Transport) are widely used in these environments to ensure reliable and secure data exchange.
Moreover, the increasing focus on automation and robotics in various industries is driving the need for communication protocols that can support the integration of different systems and devices. For instance, in the automotive industry, communication protocols like CAN (Controller Area Network) and FlexRay are used to enable communication between various electronic control units (ECUs) in a vehicle.
The market for communication protocols in integrated systems is highly competitive, with several major players dominating the industry. Companies such as Siemens, Schneider Electric, ABB, and Rockwell Automation are some of the key players in this market. These companies offer a wide range of communication protocols that cater to different industry requirements and standards.
In conclusion, the market for communication protocols in integrated systems is witnessing significant growth due to the increasing adoption of IoT technology, the rise of Industry 4.0, and the demand for automation and robotics. As industries become more interconnected and reliant on seamless communication, the need for efficient and reliable communication protocols will continue to rise. Companies that can provide innovative and secure communication solutions will have a competitive edge in this growing market.
The IControl Networks Inc invention works as follows
Systems and Methods comprise a gateway which includes a processor coupled with a security system in a building via a channel. The channel is a proprietary protocol bus of the control panel for the security system. The gateway is connected to a touchscreen in the premises that displays user interfaces. Security interfaces provide access to the data collected by security systems and control functions. Network interfaces allow access to network devices. The gateway is connected to a camera located on the premises. A security server located at a distant location is connected to the gateway. The security server includes a client interface, through which remote clients exchange data with both the gateway and security system.
Background for Communication Protocols in Integrated Systems
The home and small-business security market is dominated primarily by technology providers who create comprehensive, ‘closed’ systems. Security systems are dominated by technology suppliers who build comprehensive?closed? solutions. The individual components (sensors and security panels) work only within the boundaries of one vendor’s solution. As an example, a wireless sensor from one vendor cannot be used in conjunction with a panel of security from another vendor. Each vendor has created sophisticated proprietary wireless technology to allow the installation and management wireless sensors. Wireless devices are not able to be operated independently from the vendor?s homogenous system. These traditional systems have a limited ability to connect to local or wide-area standards-based networks (such as IP networks); the majority of installed systems only support a low bandwidth, intermittent connection using phone lines or cellular backup systems. The wireless security technology of providers like GE Security and Honeywell are well-known in the industry and are examples this proprietary approach for security systems at home and business.
Due to the proprietary approach described, traditional vendors are only able to take advantage of these network functions. Even though most home and business owners have broadband access on their premises, many security systems still do not provide the advanced features associated with low-latency, high-speed LANs or WANs. The proprietary vendors are not able to provide such technology in a timely or effective manner. Three categories of solution providers are known to the art for addressing this need: traditional proprietary hardware vendors such as Honeywell, GE Security, third-party hard-wired modules providers such Alarm.com and NextAlarm; and new proprietary system providers such InGrid.
The continued exclusivity of these vendors is a disadvantage to prior art technologies. They continue to develop this technology, but it only works with hardware from the specific vendor. This ignores the need for an heterogeneous solution that is cross-vendor. Another disadvantage of prior art technologies is the inability of traditional proprietary hardware companies to create open internet-based solutions and user friendly interfaces.
A disadvantage to prior art technologies is the complexity of installation and operation, and the functional limitations that come with hardwiring new components into existing security systems. A disadvantage of prior art technologies for the new proprietary system providers is the requirement to abandon all previous technologies and implement a completely new security system in order to access new functionalities of broadband and wireless data network. It is still necessary to have systems, devices and methods which can easily interface with and control existing proprietary security technologies using a variety wireless technologies.
An integrated system is described which integrates mobile and broadband access with conventional security systems to create a tri-mode network (broadband access, GSM/cellular access, and POTS access), allowing users to stay connected remotely to their premises. The integrated system complements the existing equipment for premise security, while providing remote monitoring and control capabilities. The integrated system is wirelessly coupled with the conventional security panel and integrates into the premises network. This allows broadband access to the premise security systems. Automation devices (cameras and lamp modules) Users can add remote control devices to their home, which allow them to see and/or control live video, pictures, and/or home appliances via a personal webpage or web portal, a mobile phone, or other remote client devices. Users can receive alerts via text or email when something happens in their home.
Although this detailed description contains many specifics to illustrate the invention, those of ordinary skill will understand that the embodiments described in the present application can be modified and varied in many ways.” The following illustrative examples are presented without losing generality and without imposing any limitations on the claimed invention.
As described in this document, computer networks that are suitable for use with embodiments of the present invention include local area networks, wide area networks, Internet, or any other network services, such as the World Wide Web, a Private Internet, a Public Network, Mobile networks, Cellular networks, Value-added networks, etc. Computer devices that are connected or coupled to the network can be any device controlled by a microprocessor, which allows access to the system. This includes terminal devices such as computers, workstations and servers, minicomputers, mainframe computers laptop computers mobile computers palmtop computers hand-held computers mobile phones TV set-top box combinations. Computer networks may consist of LANs and WANs as well as Internets. Computers can be used as clients, servers or a combination of both.
The integrated security system may be part of a single or multiple system. It can also be geographically separated. The integrated system can be a component or subsystem within a single system. The integrated system can be connected to one or more components (not shown), of a host or system coupled to the system.
One or more of the components or applications that are part of an integrated security system, or a system or application with which it is connected or coupled, includes and/or operates under or in conjunction with a processor system. A processing system can include any group of processor-based computing devices or devices that operate together or components thereof. The processing system may include, for example, a portable communication device, a portable computing device, or a network server. Portable computers can include any number or combination of personal computers, digital assistants (PDAs), portable computing devices and portable communication devices. The processing system may include components of a larger computer.
The processing system of a particular embodiment comprises at least one processor, and at least memory devices or subsystems. The processing system may also include, or be coupled with, at least one database. The term “processor” is used here. As used in this document, the term “processor” refers to any type of logic processing unit. This includes one or more central processor units (CPUs), Digital Signal Processors (DSPs), Application-Specific Integrated Circuits (ASICs), etc. The processor and memory may be integrated on a single chip or distributed across a number chips or components. They can also be provided using a combination of algorithms. The methods described in this document can be implemented by one or more software algorithms, programs, firmwares, hardware components, circuitry in any combination.
The components of any system, which includes the integrated system for security, can be placed together or at different locations. Communication paths are used to connect components. They can be any type of medium that is used for transferring or communicating files. Wireless connections, wired connection, and hybrid wireless/wired are all possible communication paths. Communication paths include connections or couplings to networks such as local area networks, metropolitan area networks, wide area networks, proprietary networks, interoffice networks or backend networks and the Internet. The communication paths also include removable fixed media like floppy discs, CD-ROMs, and hard disks as well as USB connections, RS232 connections, telephones, buses, electronic mail messages, and flash RAM.
Aspects described in this document may be implemented by programming functionality into a variety circuitry including programmable devices, such as FPGAs, programmable arrays logic (PAL), electrically programmable memory and logic devices, and standard cell-based circuitry as well as ASICs. Other possibilities include microcontrollers (such as embedded microprocessors), firmware, software and embedded microprocessors. Aspects of the integrated system and its corresponding methods can be implemented in microprocessors with software-based circuit simulation, discrete logic (sequential or combinatorial), fuzzy (neural), quantum devices, custom devices, and hybrids. The underlying technologies can be implemented in a wide variety of components, e.g. metal-oxide field-effect transistors (MOSFETs) like complementary metal oxide semiconductors (CMOS), or bipolar technologies such as emitter-coupled-logic (ECL), or polymer technologies, e.g. silicon-conjugated and metal-conjugated-polymer structures, mixed analog and digital etc.
It should be noted that the system, method and/or components described herein can be described by computer-aided design tools, expressed (or shown) as data and/or instruction embodied on various computer-readable mediums in terms of their behavior, register transfer and logic component, transistor and/or layout geometries and/or any other characteristics. Computer-readable media on which formatted instructions and/or data may be embodied may include, but not be limited to, nonvolatile storage medium in various forms (e.g. optical, magnetic, or semiconductor storage media), and carrier waves, that can be used to transmit such formatted instructions and/or data through wireless, optical or wired signaling, or any combination of these. Transfers of formatted data or instructions via carrier waves can include but not be limited to transfers (uploads, downloads, email, etc.). Over the Internet or other computer networks using one or more data-transfer protocols (e.g. HTTP, FTP SMTP etc.). The above components and/or data can be received by a computer via one or multiple computer-readable media. They may then be processed in conjunction with the execution of other computer programs.
The words “comprise” are used throughout the description, and in the claims, unless the context clearly indicates otherwise. ?comprising,? The word “including” is used in an inclusive, rather than exclusive, sense. The singular and plural numbers are included in words that use the singular or plural. The words “herein” and “under” are also included. ?hereunder,? ?above,? ?below,? When words and phrases of the same import are used in this application they refer to the application as a complete document and not just to a particular section. When the word “or” is used in a list of two or more items, it can be interpreted as any one item on the list, all items in a given list, or any combination. When the word?or? is used to refer to a list with two or more items it can be interpreted in many different ways: as any one of the items on the list, as all the items on the list, and even in any combination.
The above description of embodiments for the integrated security system, and the corresponding systems and method is not meant to be exhaustive nor to limit the disclosed systems and methods. The integrated security system, including examples, is described in this document for illustration purposes. However, those who are skilled in the relevant field will be able to recognize that various modifications within the scope are possible. The integrated security system, and the corresponding systems and method described herein can also be used for other systems and methodologies.
The elements and acts described in the above embodiments can be combined into new embodiments. In light of this detailed description, these and other changes may be made to an integrated security system as well as corresponding systems and methodologies.
According to the embodiments described in this document, a wireless (e.g. radio frequency) system is provided. This system allows a consumer or security provider to upgrade a non RF capable security system to include RF capabilities. The system comprises an RF capable Gateway device (physically situated within RF range) and software running on the Gateway device. The system includes a remote database, web server and application server that provide a persistent storage for system information.
The security systems of one embodiment, referred herein as iControl security or integrated security systems, extend the value and benefits of traditional home security through broadband access, remote monitoring, and home control. This is done by forming a security network that includes components of the integrated system integrated with a conventional premise system and a premise area network (LAN). The integrated security system allows home security devices such as cameras, touchscreens, lighting controls and/or Internet Protocol devices to be connected. These devices can then be accessed anywhere from a mobile phone, web browser or content-enabled touch screens. “The integrated security system allows security operators both to extend the value proposition for their monitored security systems, and to reach new consumers including broadband users who are interested in staying connected with their family, their home and their property while they are away from their home.
The integrated security system according to an embodiment comprises security servers (also referred herein to as iConnect or security network server) and an iHub (also referred herein to as the gateway or the iHub) gateway that integrates or couples into a home networking (e.g. LAN) in order to communicate directly with the security panel. This is true for both wired or wireless installations. The embodiment’s security system automatically detects security system components, such as sensors. The gateway is connected to the control panel and the security system, and allows consumers to access the system in both directions via mobile and web portals. The gateway can connect to a variety of security systems and control panels. It supports wireless protocols. Users and service providers can extend the capabilities of the system with additional IP cameras, security devices like interactive touchscreen keypads or lighting modules. This integrated system provides a higher level of value by allowing consumers to remain connected via email and SMS notifications, photo pushes, event-based video recording, and rule-based monitoring. This solution expands the reach and capability of home security for households with broadband access.
The integrated security system is a system that builds on the traditional security system by adding broadband and mobile access to it, as well as IP cameras, touchscreens and an open approach for home automation. The integrated system can be easily managed and installed by the security operator. It simplifies the traditional installation process.
Click here to view the patent on Google Patents.